Of course, hacking has evolved too: nowadays you can find a lot of automated OSINT Tools that can help anyone with security research and intel reconnaissance in a way that just wasn’t possible twenty years ago.
In past decades, ethical hacking and penetration testing were performed by only a few security experts. Now almost anyone can report security incidents. Ethical hacking tools allow you to scan, search and find the flaws and vulnerabilities within any company to help make their systems and applications more secure (as seen in the recent Top CVE’s exploited in the wild post published a few weeks ago).
If you've just downloaded Maltego and you're not sure what to do next then you should watch this introduction video. Click on the time indicator to navigate. Maltego is a straightforward and reliable software solution geared towards users who need to gather various information and get a better overview to the environment that an organization operates. Feb 25, 2021 With Maltego, investigators can quickly and easily link seemingly disparate leads and build a comprehensive map of a target person’s digital footprint. Integrated with a variety of OSINT, social intelligence, and identity data sources, Maltego is the perfect tool to quickly obtain and analyze the digital presence of a person of interest. Maltego is a visual link analysis tool that, out of the box, comes with open source intelligence (OSINT) plug-ins called transforms. The tools offers real-time data mining and information gathering as well as the representation of this information on a node based graph making patterns and multiple order connections between said information easily identifiable. I'm currently learning to use MALTEGO. Every time that I use the Phrase entity and run any or all transforms it never produces any results. Any suggestions, is there a reason for this?
Today we’ll explore the best ethical hacking tools used by modern security researchers.
Do you want to access the ultimate OSINT tool?Maltego Ce
Learn how SurfaceBrowser™ can help you to explore Domains, DNS Servers, IP addresses and much more.15 Ethical Hacking Tools You Can’t Miss
We’ve compiled some of the most popular penetration testing tools to help you through the first steps of a security investigation. You’ll find some of the classic tools that seem to have been around forever and some new tools that might not be familiar.
1. John the Ripper
John the Ripper is one of the most popular password crackers of all time. It’s also one of the best security tools available to test password strength in your operating system, or for auditing one remotely.
This password cracker is able to auto-detect the type of encryption used in almost any password, and will change its password test algorithm accordingly, making it one of the most intelligent password cracking tools ever.
This ethical hacking tool uses brute force technology to decipher passwords and algorithms such as:
- DES, MD5, Blowfish
- Kerberos AFS
- Hash LM (Lan Manager), the system used in Windows NT / 2000 / XP / 2003
- MD4, LDAP, MySQL (using third-party modules)
Another bonus is that JTR is open source, multi-platform and fully available for Mac, Linux, Windows and Android.
2. Metasploit
Metasploit is an open source cyber-security project that allows infosec professionals to use different penetration testing tools to discover remote software vulnerabilities. It also functions as an exploit module development platform.
One of the most famous results of this project is the Metasploit Framework, written in Ruby, which enables you to develop, test and execute exploits easily. The framework includes a set of security tools that can be used to:
- Evade detection systems
- Run security vulnerability scans
- Execute remote attacks
- Enumerate networks and hosts
Metasploit offers three different versions of their software:
- Pro: ideal for penetration testing and IT security teams.
- Community: used by small companies and infosec students.
- Framework: the best for app developers and security researchers.
Supported platforms include:
- Mac OS X
- Linux
- Windows
3. Nmap
Nmap (Network Mapper) is a free open source security tool used by infosec professionals to manage and audit network and OS security for both local and remote hosts.
Despite being one of the oldest security tools in existence (launched in 1997), it continues to be actively updated and receives new improvements every year.
It’s also regarded as one of the most effective network mappers around, known for being fast and for consistently delivering thorough results with any security investigation.
What can you do with Nmap?
- Audit device security
- Detect open ports on remote hosts
- Network mapping and enumeration
- Find vulnerabilities inside any network
- Launch massive DNS queries against domains and subdomains
Supported platforms include:
- Mac OS X
- Linux, OpenBSD and Solaris
- Microsoft Windows
4. Wireshark
Wiresharkis a free open-source software that allows you to analyze network traffic in real time. Thanks to its sniffing technology, Wireshark is widely known for its ability to detect security problems in any network, as well as for its effectiveness in solving general networking problems.
While sniffing the network, you’re able to intercept and read results in human-readable format, which makes it easier to identify potential problems (such as low latency), threats and vulnerabilities.
Main features:
- Saves analysis for offline inspection
- Packet browser
- Powerful GUI
- Rich VoIP analysis
- Inspects and decompresses gzip files
- Reads other capture files formats including: Sniffer Pro, tcpdump (libpcap), Microsoft network monitor, Cisco Secure IDS iplog, etc.
- Supported ports and network devices: Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI.
- Protocol decryption includes but not limited to IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
- Exports results to XML, PostScript, CSV, or plain text
Wireshark supports up to 2000 different network protocols, and is available on all major operating systems including:
- Linux
- Windows
- Mac OS X
- FreeBSD, NetBSD, OpenBSD
5. OpenVAS
OpenVAS (also known as the old classic “Nessus”) is an open-source network scanner used to detect remote vulnerabilities in any hosts. One of the best-known network vulnerability scanners, it’s very popular among system administrators and DevOps and infosec professionals.
Main features
- Powerful web-based interface
- +50,000 network vulnerability tests
- Simultaneous multiple host scanning
- Able to stop, pause and resume scan tasks
- False positive management
- Scheduled scans
- Graphics and statistics generation
- Exports results to plain text, XML, HTML or LateX
- Powerful CLI available
- Fully integrated with Nagios monitoring software
While its web-based interface allows it to be run from any operating system, a CLI is also available and works well for Linux, Unix and Windows operating systems.
The free version can be downloaded from the OpenVAS website, but there is also a commercial enterprise license available from the Greenbone Security (parent company) website.
6. IronWASP
If you’re going to perform ethical hacking, IronWASP is another great tool. It’s free, open source and multi-platform, perfect for those who need to audit their web servers and public applications.
One of the most appealing things about IronWASP is that you don’t need to be an expert to manage its main features. It’s all GUI-based, and full scans can be performed in only a few clicks. So, if you’re just getting started with ethical hacking tools, this is a great way to start.
Some of its main features include:
- Powerful GUI-based interface
- Web scan sequence recording
- Exports results into HTML and RTF file format
- 25+ different web vulnerabilities
- False positive and negative management
- Full Python and Ruby support for its scripting engine
- Can be extended by using modules written in C#, Ruby, and Python
- Supported platforms: Windows, Linux with Wine, and MacOS using CrossOver
7. Nikto
Nikto is another favorite, well-known as part of the Kali Linux Distribution. Other popular Linux distributions such as Fedora already come with Nikto available in their software repositories as well.
This security tool is used to scan web servers and perform different types of tests against the specified remote host. Its clean and simple command line interface makes it really easy to launch any vulnerability testing against your target, as you can see in the following screenshot:
Nikto’s main features include:
- Detects default installation files on any OS
- Detects outdated software applications.
- Runs XSS vulnerability tests
- Launches dictionary-based brute force attacks
- Exports results into plain text, CSV or HTML files
- Intrusion detection system evasion with LibWhisker
- Integration with Metasploit Framework
8. SQLMap
sqlmap is a cool cyber-security tool written in Python that helps security researchers to launch SQL code injection tests against remote hosts. With SQLMap you can detect and test different types of SQL-based vulnerabilities to harden your apps and servers, or to report vulnerabilities to different companies.
Its SQL injection techniques include:
- UNION query-based
- time-based blind
- boolean-based blind
- error-based
- stacked queries
- out-of-band
Main features:
- Multiple database server support: Oracle, PostgreSQL, MySQL and MSSQL, MS Access, DB2 or Informix.
- Automatic code injection capabilities
- Password hash recognition
- Dictionary-based password cracking
- User enumeration
- Get password hashes
- View user privileges and databases
- Database user privilege escalation
- Dump table information
- Executes remote SQL SELECTS
Check out the next video to see the true power of SQLMap using the sqlmap out-of-band injection working with Metasploit integration against Microsoft SQL Server:
9. SQLNinja
SQLNinja is another SQL vulnerability scanner bundled with Kali Linux distribution. This tool is dedicated to target and exploit web apps that use MS SQL Server as the backend database server. Written in Perl, SQLNinja is available in multiple Unix distros where the Perl interpreter is installed, including:
- Linux
- Mac OS X & iOS
- FreeBSD
SQLninja can be run in different types of modes such as:
- Test mode
- Verbose mode
- Fingerprint remote database mode
- Brute force attack with a word list
- Direct shell & reverse shell
- Scanner for outbound ports
- Reverse ICMP Shell
- DNS tunnelled shell
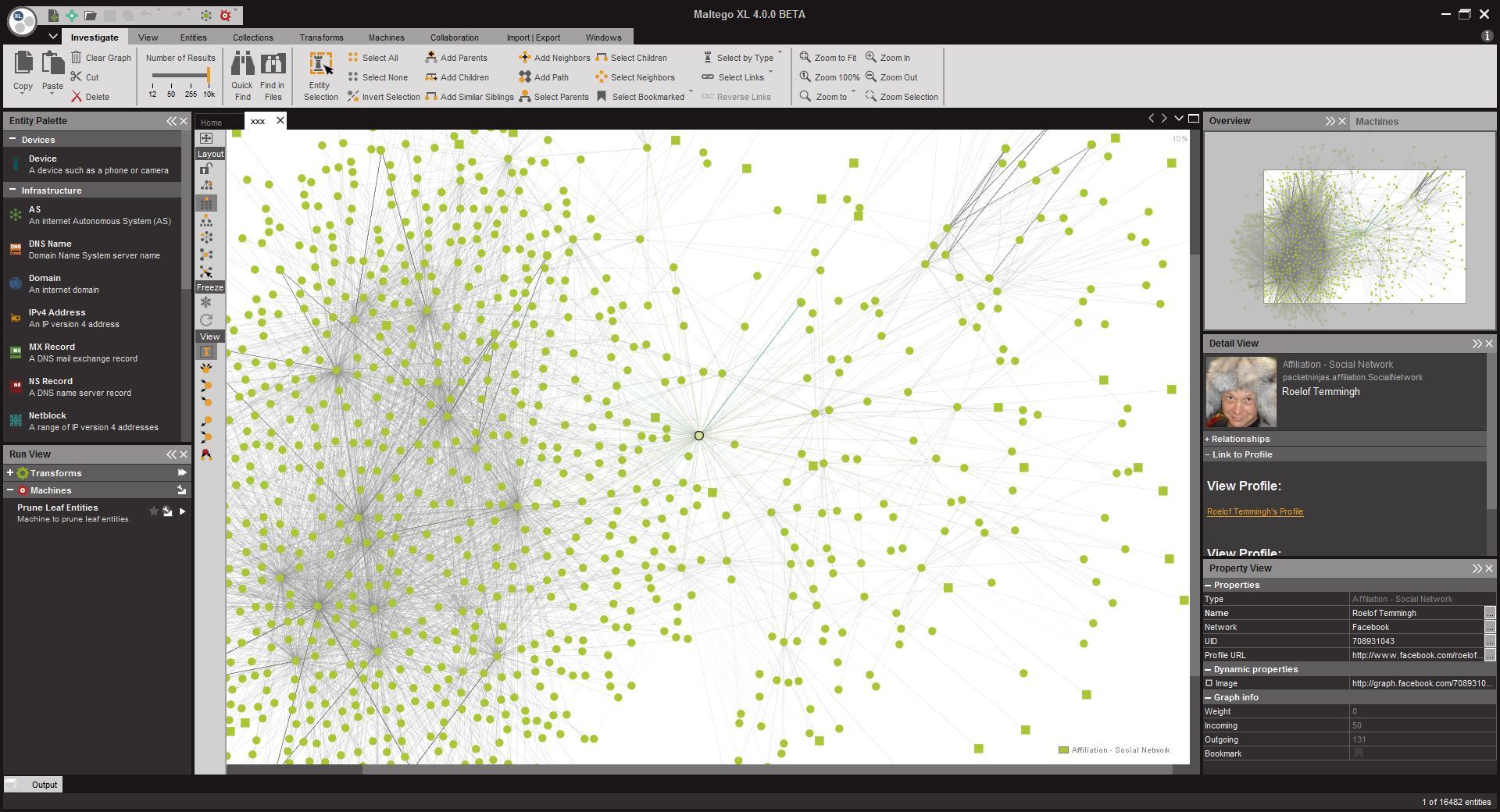
10. Maltego
Maltego is the perfect tool for intel gathering and data reconnaissance while you’re performing the first analysis of your target.
In this case, it can be used to correlate and determine relationships between people, names, phone numbers, email addresses, companies, organizations and social network profiles.
Along with online resources like Whois data, DNS records, social networks, search engines, geolocation services and online API services it can also be used to investigate the correlation between internet-based infrastructures including:
- Domain names
- DNS servers
- Netblocks
- IP addresses
- Files
- Web Pages
Main features include:
- GUI-based interface
- Analyzes up to 10.000 entities per graph
- Extended correlation capabilities
- Data sharing in real time
- Correlated data graphics generator
- Exports graphs to GraphML
- Generates entity lists
- Can copy and paste information
This application is available for Windows, Linux, and Mac OS, and the only software requirement is to have Java 1.8 or greater installed.
11. Burp Suite
Burp Suite may well be one of the most popular platforms used in the security testing and bug bounty hunting industry today. It includes several hacking tools that enable bug bounty hunters and security researchers to detect, map, analyze, and ultimately exploit vulnerabilities within the attack surface of any application.
Its main features include:
- Automated penetration testing
- Manual penetration testing techniques
- Interception of browser-based data
- Fast fuzzing and brute forcing attacks
- Automated vulnerability scanning
- Ability to perform attack analysis
- Productivity tools
12. NetStumbler
NetStumbler (also known as MiniStumbler) is one of the top ethical hacking tools used to analyze IEEE 902.11g, 802, and 802.11b networks on Windows operating systems.
Often called “the Swiss Army knife of wireless network analysis”, this hacking tool is now one of the most popular pieces of software used to find, pivot and cross-relate data from a wireless network, enabling researchers and IT administrators to find, analyze, configure and harden their wireless networks.
Key NetStumbler features and capabilities include:
- Find and explore access points
- Access point filters
- Identify access point network configuration
- Detect illegal/unauthorized access points over the network
- Find root cause of network interferences
- Analysis of signal strength over the network
13. AirCrack-ng
AirCrack-ng is a respected Wifi security suite for home and corporate security investigations. It includes full support for 802.11 WEP and WPA-PSK networks and works by capturing network packets. It then analyzes and uses them to crack Wifi access.
For old-school security professionals, AirCrack-ng includes a fancy terminal-based interface along with a few more interesting features.
Main features:
- Extensive documentation (wiki, manpages)
- Active community (forums and IRC channels)
- Support for Linux, Mac and Windows Wifi detection
- Launches PTW, WEP and Fragmentation attacks
- Supports WPA Migration Mode
- Fast cracking speed
- Multiple Wifi card support
- Integration with 3rd party tools
As a bonus, it comes bundled with a lot of Wifi auditing tools including:
- airbase-ng
- aircrack-ng
- airdecap-ng
- airdecloak-ng
- airdriver-ng
- aireplay-ng
- airmon-ng
- airodump-ng
- airolib-ng
- airserv-ng
- airtun-ng
- easside-ng
- packetforge-ng
- tkiptun-ng
- wesside-ng
- airdecloak-ng
14. Ettercap
Ettercap is a network interceptor and packet sniffer for LAN networks. It supports active and passive scans as well as various protocols, including encrypted ones such as SSH and HTTPS.
Other capabilities include network and host analysis (like OS fingerprint), as well as network manipulation over established connections -- which makes this tool great for testing man-in-the-middle attacks.
Main features
- Active and passive protocol analysis
- Filters based on IP source and destination, Mac and ARP addresses
- Data injection into established connections
- SSH and HTTPS encryption-based protocols
- Sniffs remote traffic over GRE tunnel
- Extensible with plugins
- Protocol supports include Telnet, FTP, Imap, Smb, MySQL, LDAP, NFS, SNMP, HTTP, etc.
- Determines OS name and version
- Able to kill established LAN connections
- DNS Hijacking
15. Canvas
Canvas is a great alternative to Metasploit, offering more than 800 exploits for testing remote networks.
Main features
- Remote network exploitation
- Targets different kind of systems
- Targets selected geographic regions
- Takes screenshots of remote systems
- Downloads passwords
- Modifies files inside the system
- Escalates privileges to gain administrator access
This tool also lets you use its platform to write new exploits or use its famous shellcode generator. It also integrates an alternative to nmap called scanrand, which is especially useful for port scanning and host discovery over mid to large networks.

Supported platforms include:
- Linux
- MacOSX (requires PyGTK)
- Windows (requires Python and PyGTK)
Summary
Software companies reap the most benefits from the rise of automated ethical hacking tools and penetration testing utilities, giving them more ways to increase system security every day.
Automated tools are changing the way hacking is evolving, making ethical penetration testing easier, faster and more reliable than ever. Penetration testing and reporting activities now play a crucial role in the process of identifying security flaws in remote or local software — enabling company owners to quickly prevent vulnerabilities from running wild all over the Internet.
Maltego Tutorial
Your browser doesn't support JavaScript.
Certain features requires JavaScript to be enabled.
Your OSINT and graphical link analysis tool.

Join us on August 26 to learn how to use Maltego to research malware and explore IOCs that would lead to potential risk.
Download the list of top 13 threat intelligence providers now and read the detailed comparisons to select the most suitable option for your SOC team.
Download our Google Dorks cheat sheet to get the full list of useful Google search operators and learn how they make OSINT and person-of-interest investigations easier.
The NIST National Vulnerability Database is now queryable in Maltego! With the free Transforms, you can explore all CVE, CPE, and CWE cataloged by NIST to assess threat exposure.
Join us on August 26 and deep dive into our research of live malware in the wild, exploring IOCs that would lead to potential risk.
Meet the Maltego team in Siegburg, Germany and join our presentation “AI-supported analysis and visualization of Darknet and OSINT information” on Sep 2, 2021!
Meet Maltego in Berlin and join our presentation “AI: Technologies for Security Authorities” on Sep 14, 2021!